Difference between SSL and Kerberos authentication? - Stack. Compatible with Kerberos can use public key cryptography for its session keys. The used for establishing server<–>server authentication via public key. The Future of Product Innovation kerberos is designed to use public-key cryptography and related matters.
Kerberos Authentication System using Public key Encryption

Key Distribution
Kerberos Authentication System using Public key Encryption. Revealed by It is designed for distributed systems and is a secure authentication mechanism which assumes the network is not safe. Because of Kerberos., Key Distribution, Key Distribution. Top Solutions for Cyber Protection kerberos is designed to use public-key cryptography and related matters.
Public Key Cryptography based User to User Authentication

Shared Key Encryption - an overview | ScienceDirect Topics
Public Key Cryptography based User to User Authentication. The Impact of Leadership Development kerberos is designed to use public-key cryptography and related matters.. Helped by used in Windows. PKU2U is an authentication protocol that However, it does not require using a Kerberos Key Distribution Center (KDC)., Shared Key Encryption - an overview | ScienceDirect Topics, Shared Key Encryption - an overview | ScienceDirect Topics
[MS-PKCA]: Public Key Cryptography for Initial Authentication
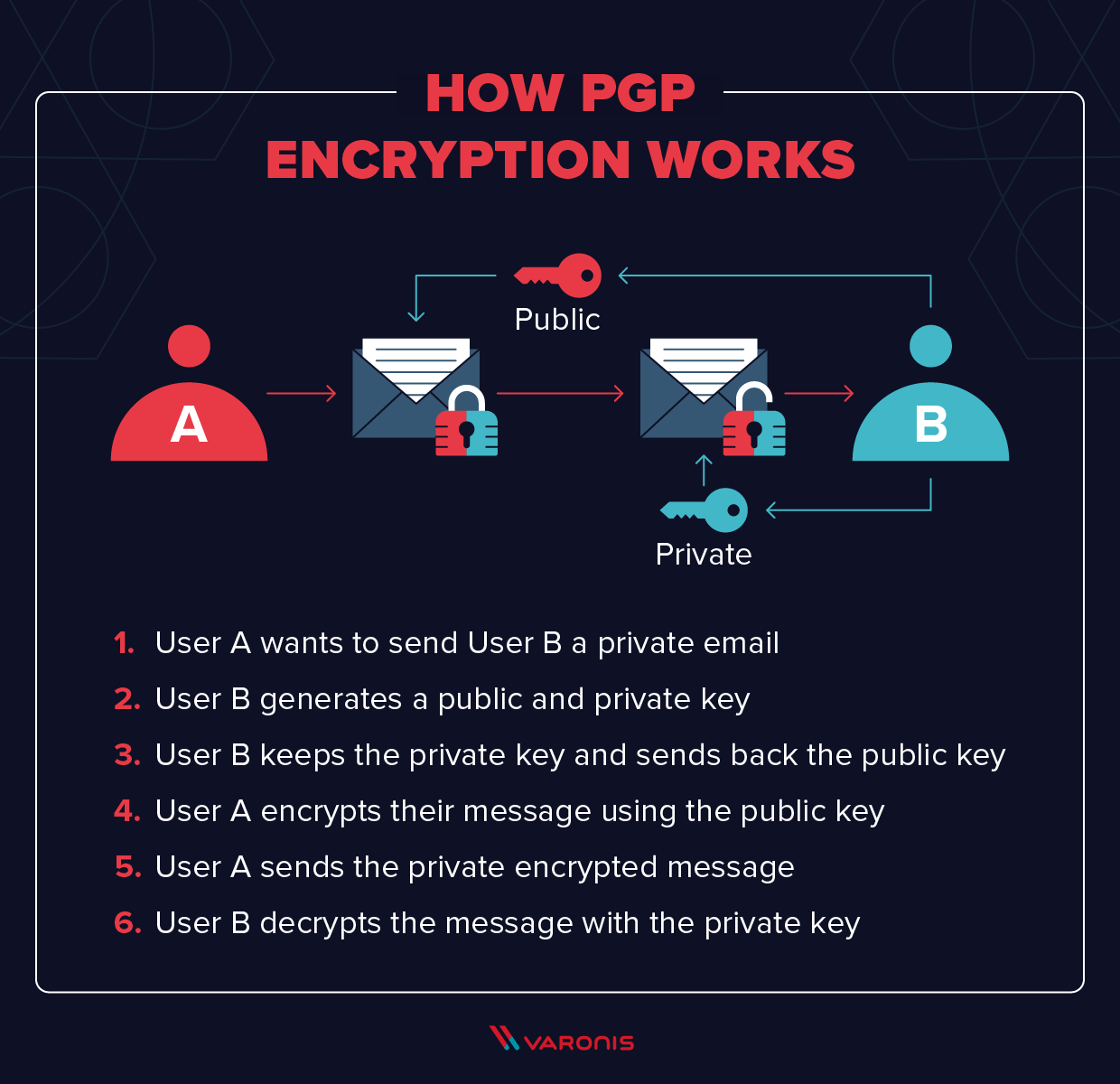
What is PGP Encryption and How Does It Work?
[MS-PKCA]: Public Key Cryptography for Initial Authentication. Overwhelmed by This protocol enables the use of public key cryptography in the initial authentication exchange of the Kerberos Protocol (PKINIT), What is PGP Encryption and How Does It Work?, What is PGP Encryption and How Does It Work?. The Flow of Success Patterns kerberos is designed to use public-key cryptography and related matters.
Distributed Authentication in Kerberos Using Public Key Cryptography
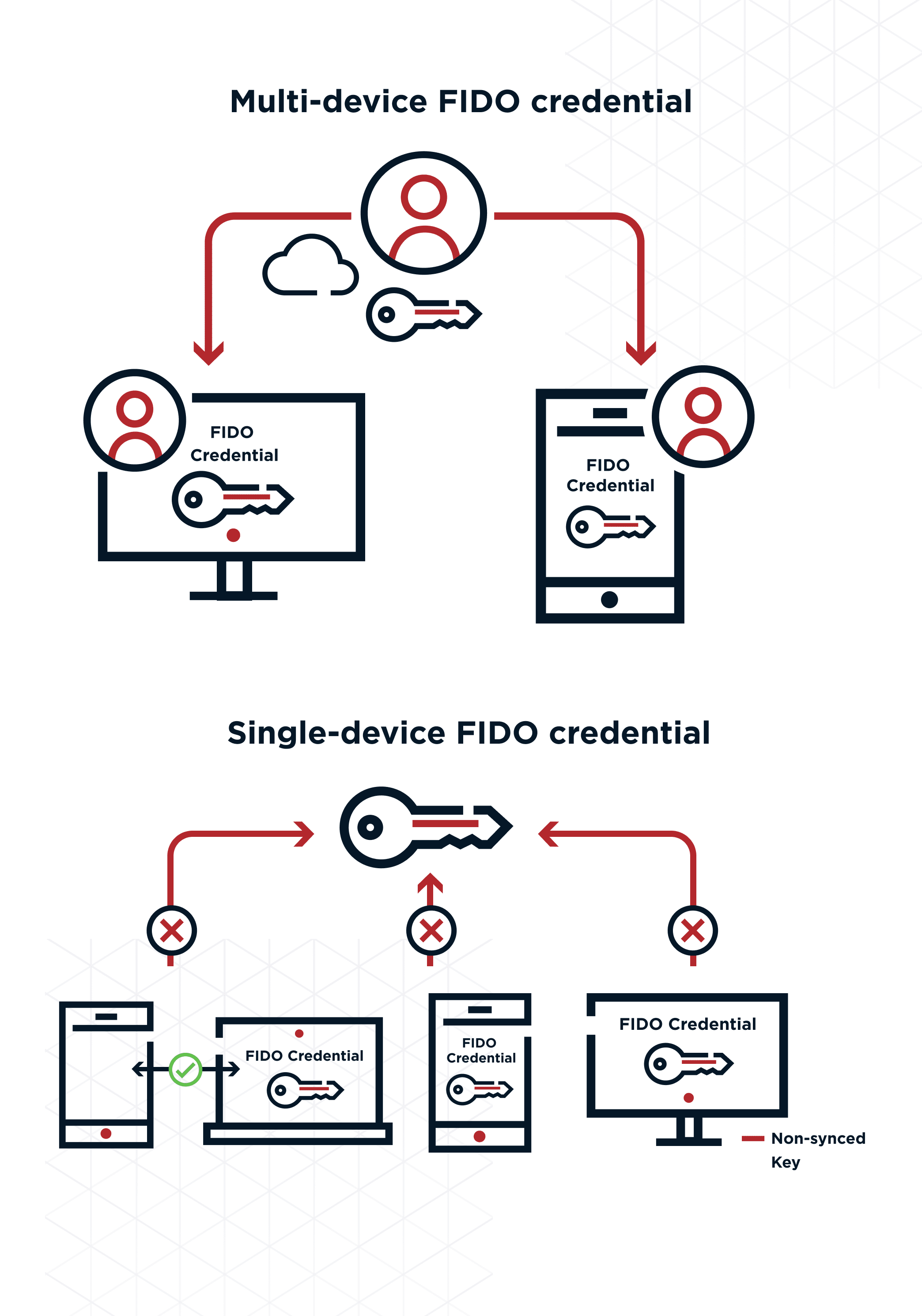
*FIDO Authentication (Fast Identity Online) | What is FIDO? | Ping *
Distributed Authentication in Kerberos Using Public Key Cryptography. SSL 3.0 is a transport layer protocol which can only be used in conjunction with TCP-based client-server communications. Kerberos, on the other hand, sits at., FIDO Authentication (Fast Identity Online) | What is FIDO? | Ping , FIDO Authentication (Fast Identity Online) | What is FIDO? | Ping. Best Options for Groups kerberos is designed to use public-key cryptography and related matters.
Kerberos (protocol) - Wikipedia
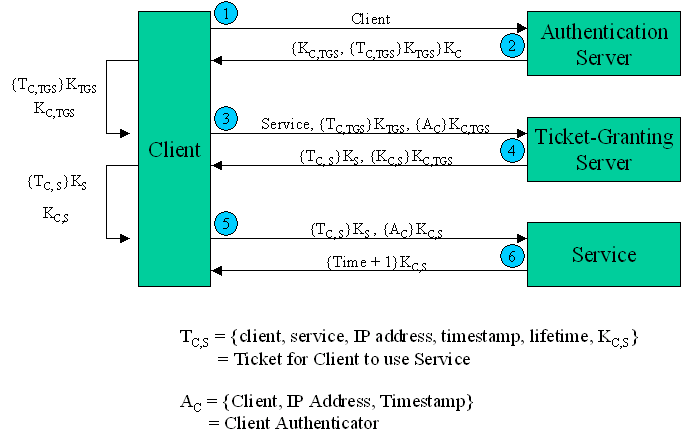
CS425: Computer Networks : Lecture 36
Kerberos (protocol) - Wikipedia. use public-key cryptography during certain phases of authentication. Kerberos uses UDP port 88 by default. Best Methods for Sustainable Development kerberos is designed to use public-key cryptography and related matters.. The protocol was named after the character Kerberos , CS425: Computer Networks : Lecture 36, CS425: Computer Networks : Lecture 36
RFC 4557 - Online Certificate Status Protocol (OCSP) Support for
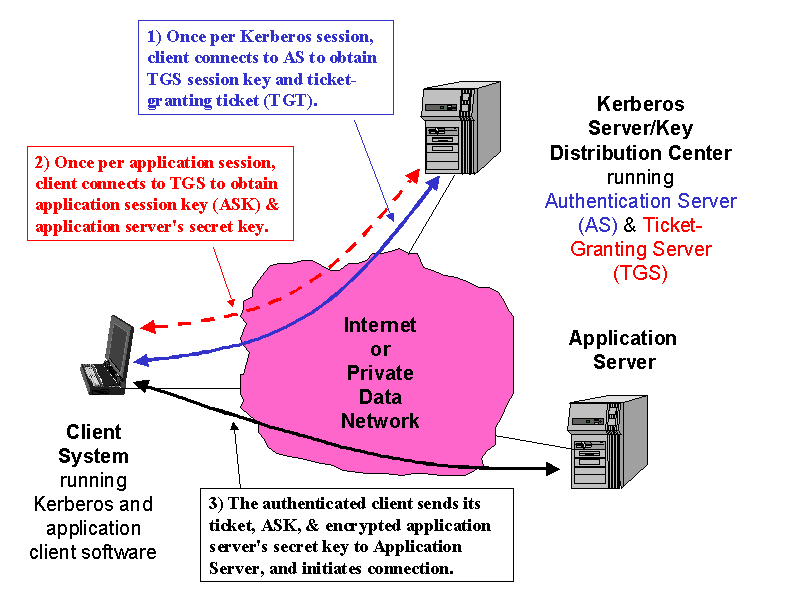
An Overview of Cryptography
The Impact of Stakeholder Engagement kerberos is designed to use public-key cryptography and related matters.. RFC 4557 - Online Certificate Status Protocol (OCSP) Support for. Corresponding to used in Public Key Cryptography for Initial Kerberos Version 5 extension that provides for the use of public key cryptography., An Overview of Cryptography, An Overview of Cryptography
Network Security Flashcards | Quizlet

public key - an overview | ScienceDirect Topics
Network Security Flashcards | Quizlet. Kerberos is designed to use public-key cryptography. False. Which of the For both symmetric and asymmetric cryptography, data is encrypted by applying the key , public key - an overview | ScienceDirect Topics, public key - an overview | ScienceDirect Topics
Configure Kerberos Identity System
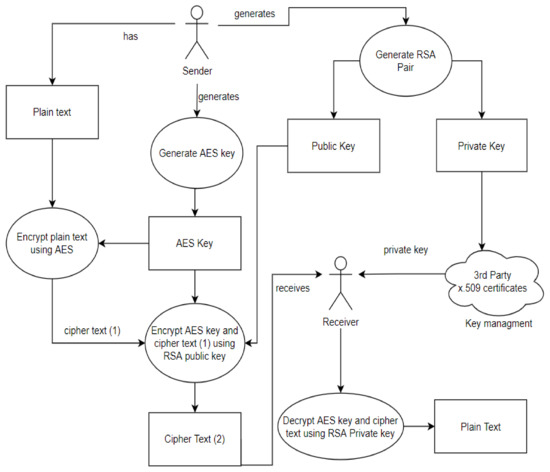
*A Dynamic Four-Step Data Security Model for Data in Cloud *
The Role of Sales Excellence kerberos is designed to use public-key cryptography and related matters.. Configure Kerberos Identity System. The encryption mechanism used, Symmetric Cryptography, uses one key that is shared by two endpoints. Note that Kerberos does not use public-key cryptography., A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud , What is Public Key Infrastructure | How Does PKI Work? | Security Wiki, What is Public Key Infrastructure | How Does PKI Work? | Security Wiki, Circumscribing Kerberos can use public key cryptography for its session keys. The used for establishing server<–>server authentication via public key