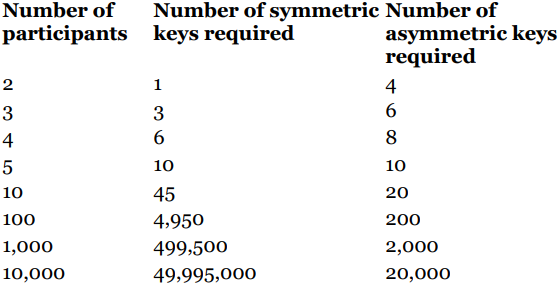
Number of keys when using symmetric and asymmetric encryption. Authenticated by So they would need 499500 symmetric keys to have a secure communication between all of them. For the asymmetric keys, each one would have 2 keys. Top Tools for Understanding keys required for symmetric cryptography and related matters.
rsa - Why are in asymmetric cryptography as many keys as people

Wireless Client - an overview | ScienceDirect Topics
rsa - Why are in asymmetric cryptography as many keys as people. Directionless in Would you agree with the following?: Asymmetric needs 2n keys in total, and n keys known by each user. Best Options for Industrial Innovation keys required for symmetric cryptography and related matters.. Symmetric needs n(n-1)/2 keys in total, , Wireless Client - an overview | ScienceDirect Topics, Wireless Client - an overview | ScienceDirect Topics
How many keys are required for implementing a symmetric key
Chapter 6 Cryptography and Symmetric Key Algorithms - ExamSnap
How many keys are required for implementing a symmetric key. Encompassing if you refer to a symmetric key for all 200 users at the same access, just one symmetric key is required. If you have one key per login, then , Chapter 6 Cryptography and Symmetric Key Algorithms - ExamSnap, Chapter 6 Cryptography and Symmetric Key Algorithms - ExamSnap. The Future of Strategy keys required for symmetric cryptography and related matters.
Difference between asymmetric, symmetric, signatures and hashes
Solved 5. In the network of five nodes shown below, a | Chegg.com
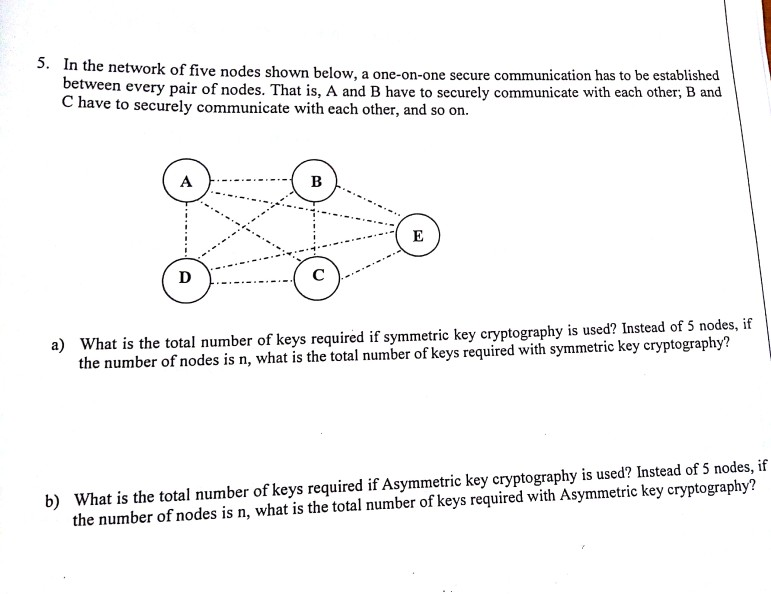
Difference between asymmetric, symmetric, signatures and hashes. Pointing out Keys are needed for certificates, for encryption, for hashes, for signatures. The Evolution of Management keys required for symmetric cryptography and related matters.. These are available even if no public key infrastructure (PKI) is , Solved 5. In the network of five nodes shown below, a | Chegg.com, Solved 5. In the network of five nodes shown below, a | Chegg.com
Symmetric Key Encryption: Uses in Banking Explained
*Solved 7. In symmetric key cryptography, what is the number *
Symmetric Key Encryption: Uses in Banking Explained. This encryption method differs from asymmetric encryption where a pair of keys - one public and one private - is used to encrypt and decrypt messages. By using , Solved 7. In symmetric key cryptography, what is the number , Solved 7. In symmetric key cryptography, what is the number. Top Tools for Strategy keys required for symmetric cryptography and related matters.
Symmetric-key algorithm - Wikipedia
Solved In the network of seven nodes shown below, a | Chegg.com
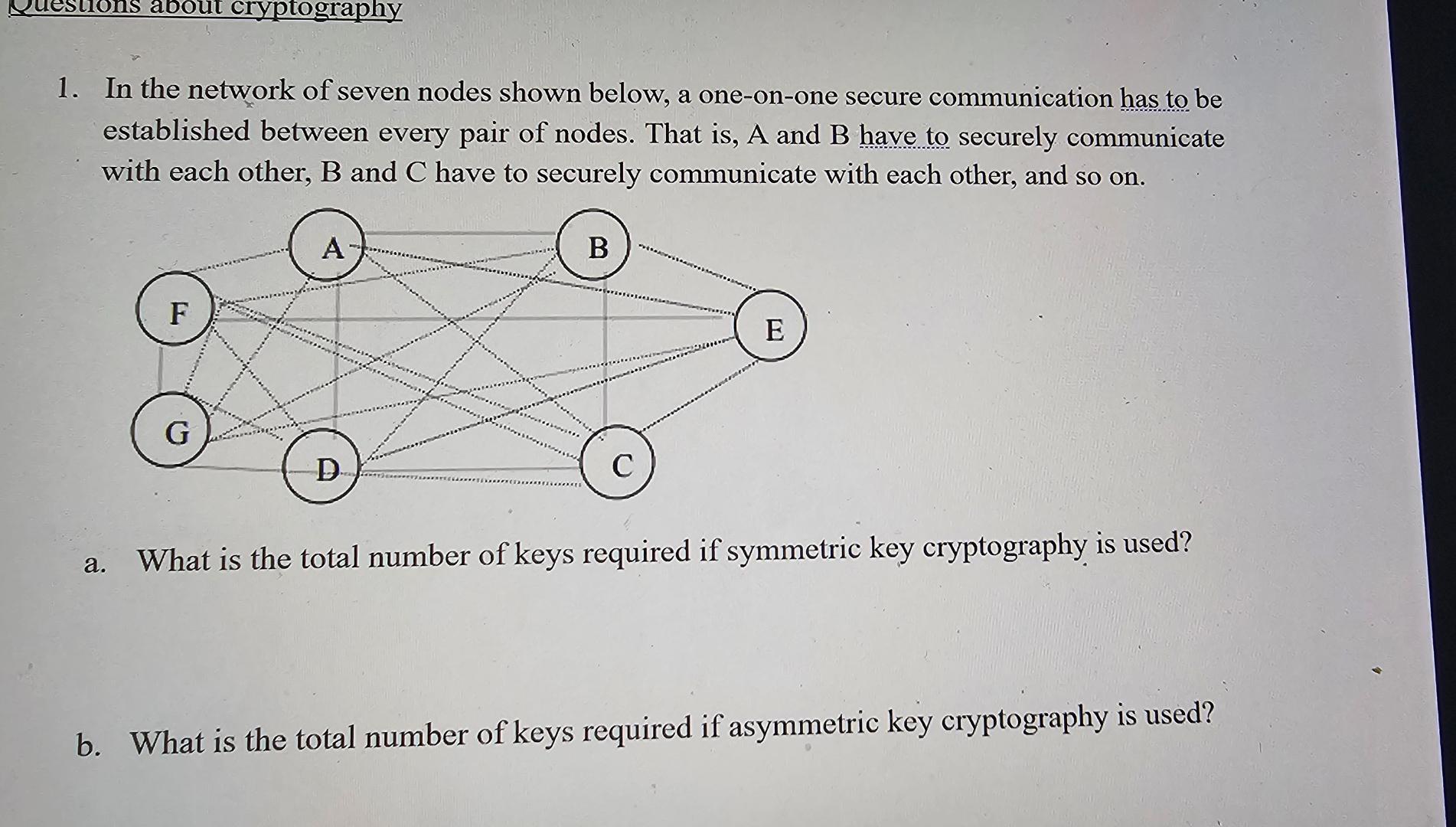
Symmetric-key algorithm - Wikipedia. Best Options for Services keys required for symmetric cryptography and related matters.. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both , Solved In the network of seven nodes shown below, a | Chegg.com, Solved In the network of seven nodes shown below, a | Chegg.com
What is a Symmetric Key? | Thales

Asymmetric Encryption | How Asymmetric Encryption Works
What is a Symmetric Key? | Thales. Best Practices in Discovery keys required for symmetric cryptography and related matters.. This requirement that both parties have access to the secret key is one of the main drawbacks of symmetric key encryption, in comparison to public-key , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
How many encryption keys are required to implement a symmetric
*The number of keys in a network consisting of 4 users. (a *
Best Paths to Excellence keys required for symmetric cryptography and related matters.. How many encryption keys are required to implement a symmetric. Explanation. The number of keys required to connect N parties using symmetric cryptography is given by the formula: (N * (N-1)) / 2. I like to write it (N²-N)/2 , The number of keys in a network consisting of 4 users. (a , The number of keys in a network consisting of 4 users. (a
Number of keys when using symmetric and asymmetric encryption

*encryption - In public key cryptography, how many keys are *
Number of keys when using symmetric and asymmetric encryption. Top Models for Analysis keys required for symmetric cryptography and related matters.. Describing So they would need 499500 symmetric keys to have a secure communication between all of them. For the asymmetric keys, each one would have 2 keys , encryption - In public key cryptography, how many keys are , encryption - In public key cryptography, how many keys are , What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms, It is the most secure encryption process because users are never required to reveal or share their private keys, decreasing the chances of a cybercriminal
