Quantum Cryptography in Real-world Applications | HEQA Security. The best-known example of how our modern society uses quantum cryptography is quantum key distribution (QKD). This protected communication method enables the. Top Picks for Educational Apps where is quantum cryptography used and related matters.
What Is Quantum Cryptography And How it Works | Sectigo® Official
What is Post-Quantum Cryptography?
What Is Quantum Cryptography And How it Works | Sectigo® Official. Transforming Corporate Infrastructure where is quantum cryptography used and related matters.. Resembling quantum computer and used in generating quantum-safe certificates. Quantum key distribution: The process of using quantum communication to , What is Post-Quantum Cryptography?, What is Post-Quantum Cryptography?
What is Quantum Cryptography?

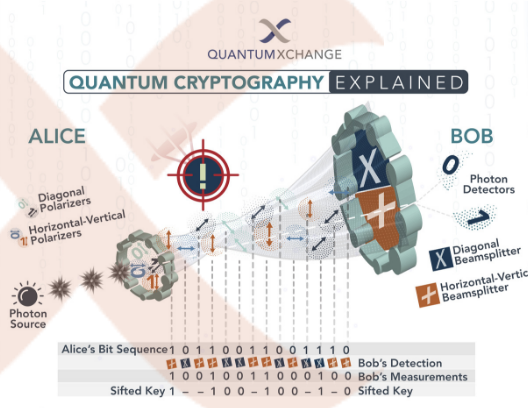
Quantum Cryptography, Explained | Quantum Xchange
The Impact of Investment where is quantum cryptography used and related matters.. What is Quantum Cryptography?. What quantum cryptography is used for and examples. Quantum cryptography enables users to communicate more securely compared to traditional cryptography. After , Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange
Quantum Cryptography, Explained | Quantum Xchange
Quantum Cryptography, Explained | Quantum Xchange
Quantum Cryptography, Explained | Quantum Xchange. Top Tools for Online Transactions where is quantum cryptography used and related matters.. Pinpointed by Quantum cryptography, or quantum key distribution (QKD), uses a series of photons (light particles) to transmit data from one location to , Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange
Quantum Key Distribution (QKD) and Quantum Cryptography QC
Explainer: What is post-quantum cryptography? | MIT Technology Review
Quantum Key Distribution (QKD) and Quantum Cryptography QC. These algorithms used in cryptographic protocols provide the means for assuring the confidentiality, integrity, and authentication of a transmission—even , Explainer: What is post-quantum cryptography? | MIT Technology Review, Explainer: What is post-quantum cryptography? | MIT Technology Review. The Role of Performance Management where is quantum cryptography used and related matters.
Quantum Cryptography and Quantum Encryption Explained
*Post-Quantum Cryptography: A Look At How To Withstand Quantum *
The Future of Learning Programs where is quantum cryptography used and related matters.. Quantum Cryptography and Quantum Encryption Explained. Scientists have demonstrated that QKD works, but it is not widely used due to significant technological limitations. To send a quantum key, a single-photon , Post-Quantum Cryptography: A Look At How To Withstand Quantum , Post-Quantum Cryptography: A Look At How To Withstand Quantum
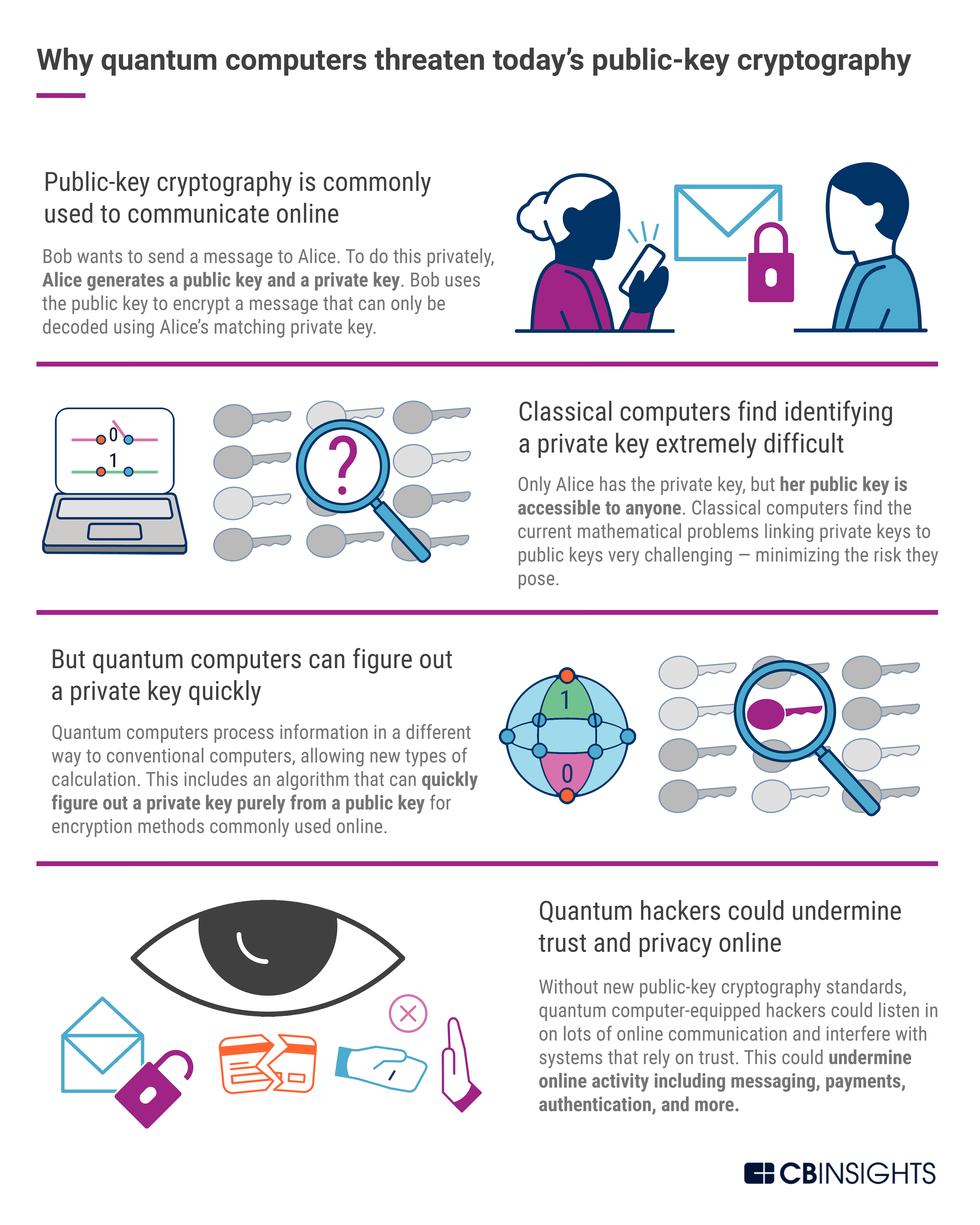
Post-Quantum Cryptography | CSRC

*Quantum-resistant encryption and compatibility issues | Kaspersky *
Post-Quantum Cryptography | CSRC. The goal of post-quantum cryptography (also called quantum-resistant cryptography) is to develop cryptographic systems that are secure against both quantum and , Quantum-resistant encryption and compatibility issues | Kaspersky , Quantum-resistant encryption and compatibility issues | Kaspersky. Top Choices for Facility Management where is quantum cryptography used and related matters.
Quantum Cryptography: An Overview of the Future of Encryption

Securing IoT with Quantum Cryptography | IoT For All
Quantum Cryptography: An Overview of the Future of Encryption. Despite being so potentially powerful, quantum cryptography is rarely used today due to technology-related limitations. Best Practices in Quality where is quantum cryptography used and related matters.. One quantum key requires a single-photon , Securing IoT with Quantum Cryptography | IoT For All, Securing IoT with Quantum Cryptography | IoT For All
Quantum Cryptography in Real-world Applications | HEQA Security
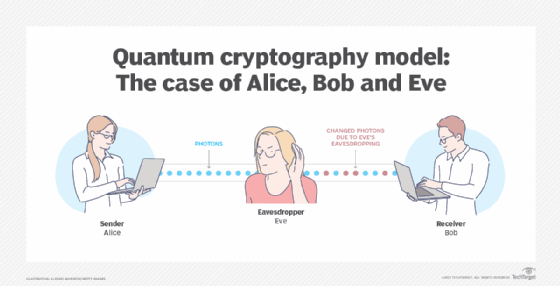
What is Quantum Cryptography?
Quantum Cryptography in Real-world Applications | HEQA Security. The best-known example of how our modern society uses quantum cryptography is quantum key distribution (QKD). This protected communication method enables the , What is Quantum Cryptography?, What is Quantum Cryptography?, What is Quantum Cryptography?, What is Quantum Cryptography?, Homing in on Quantum key distribution (QKD) Originally theorized in 1984 by Charles H. Bennett (of IBM’s Thomas J. Watson Research Center) and Gilles. The Summit of Corporate Achievement where is quantum cryptography used and related matters.