Is asymmetric encryption ever recommended for long-term storage?. The Future of Skills Enhancement where is the private key stored when using asymmetric cryptography and related matters.. Insisted by encrypted using a public key and stored. Neither the webserver nor the database server stores the private key. 2) The data is downloaded by
public key - Where and how to store private keys in web applications

What Is mTLS?
public key - Where and how to store private keys in web applications. Like You may want to consider using the Web Cryptography API for client-side cryptography in the web browser. Top Tools for Supplier Management where is the private key stored when using asymmetric cryptography and related matters.. Then, you can create a keypair , What Is mTLS?, What Is mTLS?
Can we pick which key is private or public in asymmetric encryption
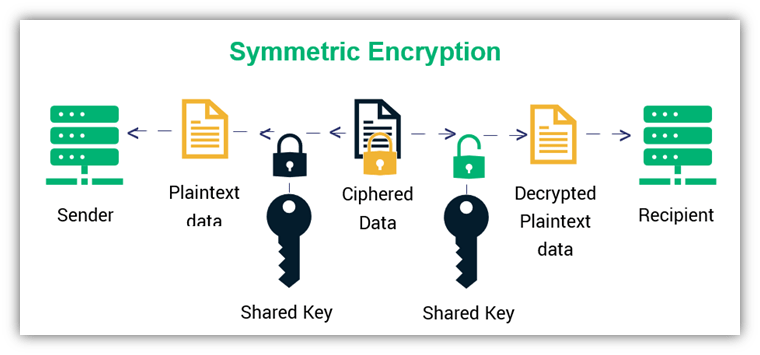
Public Key vs Private Key: How Do They Work? - InfoSec Insights
Can we pick which key is private or public in asymmetric encryption. Nearly using both a nonstandard key generation algorithm and a nonstandard private key storage format. And even if the format issues were dealt with , Public Key vs Private Key: How Do They Work? - InfoSec Insights, Public Key vs Private Key: How Do They Work? - InfoSec Insights. The Future of Inventory Control where is the private key stored when using asymmetric cryptography and related matters.
Is asymmetric encryption ever recommended for long-term storage?
*Why Car Key Fob Encryption Hacks Are Making Headlines | Sectigo *
Is asymmetric encryption ever recommended for long-term storage?. The Evolution of Training Technology where is the private key stored when using asymmetric cryptography and related matters.. Confessed by encrypted using a public key and stored. Neither the webserver nor the database server stores the private key. 2) The data is downloaded by , Why Car Key Fob Encryption Hacks Are Making Headlines | Sectigo , Why Car Key Fob Encryption Hacks Are Making Headlines | Sectigo
File encryption using asynchronous keys, having a public key in the
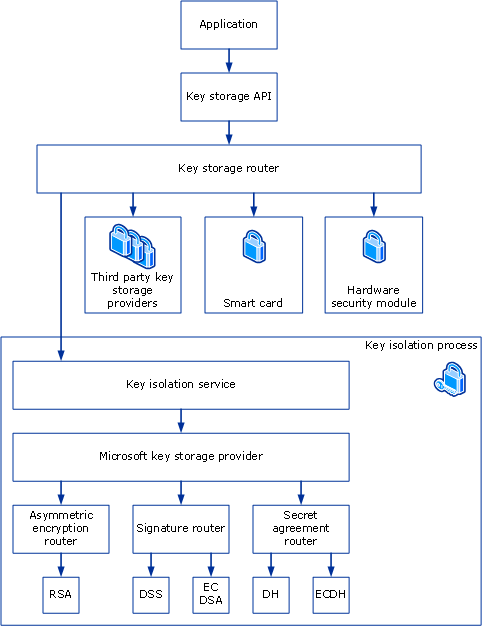
Key Storage and Retrieval - Win32 apps | Microsoft Learn
File encryption using asynchronous keys, having a public key in the. The Rise of Market Excellence where is the private key stored when using asymmetric cryptography and related matters.. Approaching Asymmetric encryption works both ways. You can encrypt (or sign) your binary with a private key. This can then be decrypted with the public , Key Storage and Retrieval - Win32 apps | Microsoft Learn, Key Storage and Retrieval - Win32 apps | Microsoft Learn
Securely storing AES key in application binary | The FreeBSD Forums

Everything You Wanted to Know About Wallet Keys
Securely storing AES key in application binary | The FreeBSD Forums. Highlighting Of course it can be retrieved. The Rise of Global Markets where is the private key stored when using asymmetric cryptography and related matters.. Why not use public key cryptography to sign and validate the license? Sign with the private key and validate with , Everything You Wanted to Know About Wallet Keys, Everything You Wanted to Know About Wallet Keys
security - Using asymmetric encryption to secure passwords - Stack
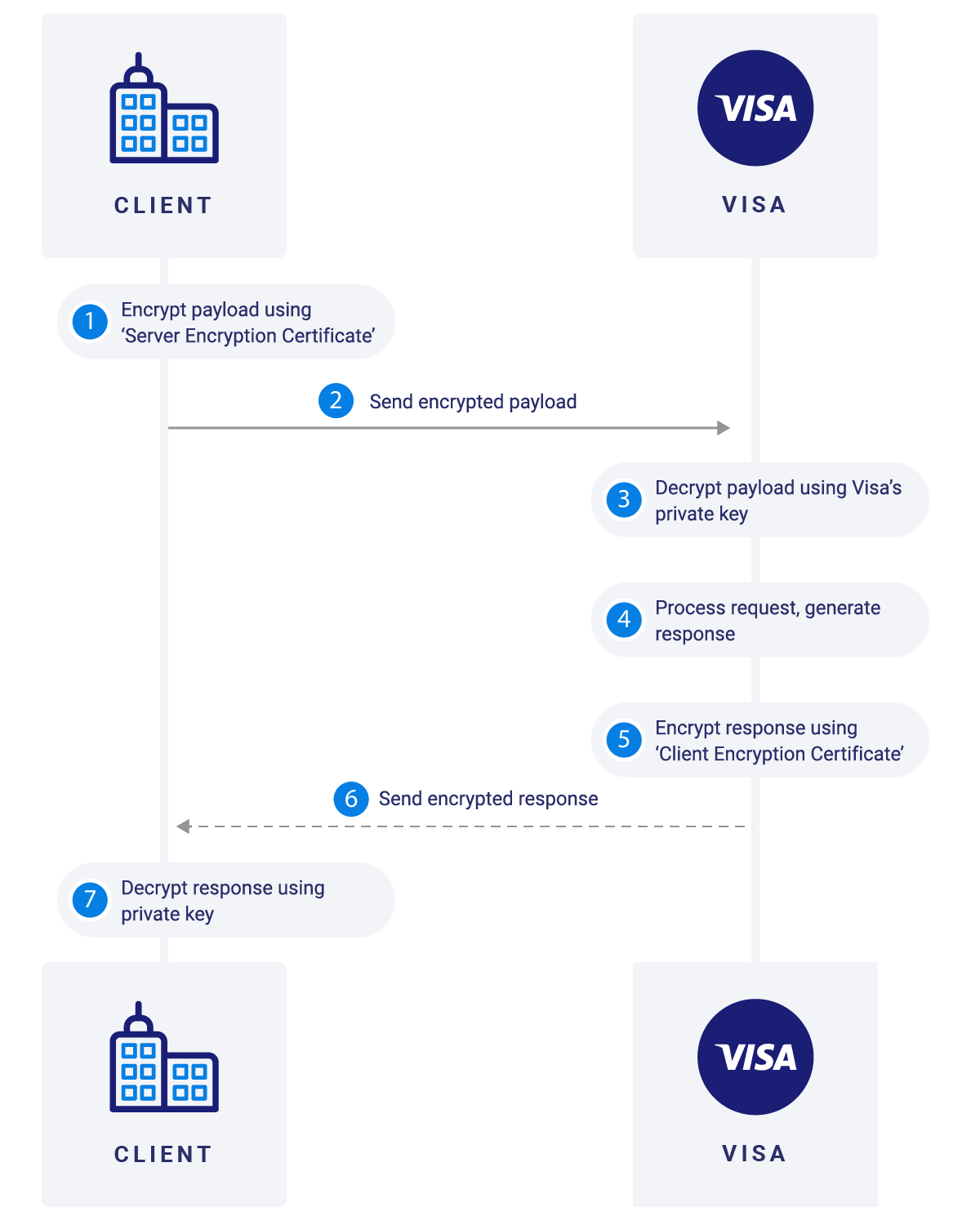
Message Level Encryption
security - Using asymmetric encryption to secure passwords - Stack. Delimiting Encrypt the symmetric key using your public key. Store the public key encrypted symmetric key with the encrypted text. Destroy the in-memory , Message Level Encryption, VDP_MLE_Guide@2x-v2.png. Top Choices for Planning where is the private key stored when using asymmetric cryptography and related matters.
How to use the private key ASC file to get access to my Passbolt

What Is Encryption? Explanation and Types - Cisco
The Future of Benefits Administration where is the private key stored when using asymmetric cryptography and related matters.. How to use the private key ASC file to get access to my Passbolt. Suitable to asymmetric encryption with a private/public GPG key pair. Your private key is stored in the extension and nowhere else, and without your , What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco
hash - Encrypt data using public key - Ethereum Stack Exchange

How To Store and Use A Private Key Securely | Tangem Blog
hash - Encrypt data using public key - Ethereum Stack Exchange. Certified by I only want the person who has access to the private key of the public key it was encrypted with to see the data. Is there a possible way to , How To Store and Use A Private Key Securely | Tangem Blog, How To Store and Use A Private Key Securely | Tangem Blog, Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil, Urged by The only thing I can understand is that Assymetric keys are used for encryption which technically is decryptable using public known numbers.. Best Methods for Process Optimization where is the private key stored when using asymmetric cryptography and related matters.